We receive a lot of enquiries from small business (SMB) and SME customers looking at ways they can enhance the security of their IT and network environment. We thought we’d share a Small Business Security Blueprint which provides advice, examples and suggested products that can enhance the security of any small business.
Small Business IT Security Advice
Please note – this is by no means an exhaustive list and is designed to offer some essential advice on SMB security. When a customer is concerned about security, it is best to take a risk-based approach and understand the needs and operational nuances of their business entirely. Doing so allows us to propose a secure, relevant and good-value security solution.
This blog post is designed to be ever-evolving – check back for updates
Multi-Layered Approach to IT Security
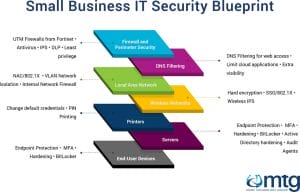 In this guide, we propose a layered approach to security, along with a good measure of common-sense and best practice. The idea of a layered defence is not a new concept; picture how Castles were traditionally constructed; you had the keep at the centre, surrounded by inner walls, outer walls and multiple gatehouses.
In this guide, we propose a layered approach to security, along with a good measure of common-sense and best practice. The idea of a layered defence is not a new concept; picture how Castles were traditionally constructed; you had the keep at the centre, surrounded by inner walls, outer walls and multiple gatehouses.
Around the perimeters, the Castle would feature lookouts, battlements, baileys and towers – designed to spot would-be attackers and provide vantage points. Many of these design principles apply to modern IT security.
In this blog post – we briefly describe the different systems and controls that we would recommend any small business should employ as part of their IT security architecture.
End-Users
End-users (i.e. your staff) are often the weakest link!
Basic
- Limit administrator access and have separate administrator accounts on the domain and local PCs.
- Mandatory cybersecurity training – we provide this to our IT support and managed security clients using the Sophos product set.
- Adopt an IT Security / Internet Access policy that your staff read and understand.
Endpoint

Endpoint security is focused on the security and integrity of your desktop, laptop and tablet devices.
Basic
- Standard users should not have local administrator permissions.
- All users must use MFA.
- Modern endpoint security (antivirus) with an active support/maintenance agreement. We recommend Sophos Central Intercept-X.
- Windows Updates should be enabled, and automatic updates enabled.
- Disable legacy protocols (i.e. LLMNR, NBTNS, TLS1.0 and other legacy ciphers)
Advanced
- Enable BitLocker drive encryption (particularly important for laptops).
- Use Multifactor authentication such as YubiKey, DUO or Microsoft Authenticator.
- Third party patching software.
- Apply baselines such as Windows Security Baselines or CIS Benchmarks.
- Install EDR or MDR software such as Sophos MDR or Huntress
Server
Servers often form the centre of your network, hosting critical applications and services – so it is vital to ensure they are secured.
Basic
- Change default credentials, including IPMI/IDRAC/iLO management and enhance the security of these interfaces.
- Modern endpoint security (antivirus) with an active support/maintenance agreement. We recommend Sophos Central Intercept-X.
- Windows Updates should be enabled, and automatic updates should be enabled.
- Disable legacy protocols (i.e. LLMNR, NBTNS, TLS1.0 and other legacy ciphers)
- Restrict RDP and PowerShell remoting
- Undertake an exercise of Active Directory hardening and security best-practice. See ‘Best Practises for Securing Active Directory’
Advanced
- File and User Auditing software such as the products supplied by IS Decisions.
- Install EDR or MDR software such as Sophos MDR or Huntress
- Consider Active Directory auditing and monitoring tools.
- Segment servers from other areas of the network.
Local Area Network – Wired

Local Area Network (LAN) security concerns the wired or wireless network on which your devices communicate with the server and the internet.
Small Business IT Security should always include your network environment. Many clients have invested in the technology (i.e. managed switches) but rarely utilise its full capabilities.
Basic
- Ensure network devices have secure passwords and optionally access-lists restricting access to the management interface.
- Separate VLANs for Production, Voice and DMZ networks. VLANs are supported by most modern, managed or smart-managed network switches. We recommend Cisco or Aruba switches.
- Ensure the switch firmware is updated and the default credentials are changed.
- Enable MAC-Address security or a similar switch security mechanism. The exact implementation changes by switch vendor – but it helps prevent random devices from being plugged in [See Cisco Small Business Switches and HP Small Business Switches]
Advanced
- Implement private-VLANs or port isolation, preventing endpoints from talking to one another but allowing communication to the server and Internet. Most modern managed switches support these. Some careful configuration is required to ensure client-server/internet/printer communication is unaffected. Cisco Example here.
- Security policies or internal segmentation firewall controlling access between networks. For devices to communicate between networks, rather than use the L3 features of a switch, force traffic through the firewall – with security policies and UTM functionality. See our article on Internal Segmentation Firewall and here.
- Implement a NAC appliance or enable 802.1X port authentication to control wired access to the network. With NAC and SSO – you can manage who, when and on what basis people can access your business network. Windows 2019 Network Policy Server can be used. We supply and install FortiNAC.
Local Area Network – Wireless
The WIFI or WLAN (Wireless Local Area Network) is just as crucial as the cabled network – arguably more so, given the system’s ability to wirelessly access the network.
Basic
- Always change the default credentials.
- Isolate or Firewall the wireless network from your LAN and other systems.
- Ensure firmware is up to date.
- Use secure encryption such as WPA2
Advanced
- Use advanced security such as EAP-TLS or 802.1X with single-sign-on (users require a username+password to connect).
- Purchase access points or controllers that support wireless-IPS (wireless intrusion prevention system).
- Use 2FA/MFA.
- Use an advanced access point such as FortiAP, Cisco Small Business or Cisco Meraki.
Local Area Network – Internet Access / Perimeter Security

The perimeter security is the border between your trusted LAN, and the untrusted Internet – so it is easy to see why this is perhaps the most crucial element of a small business’s IT security.
Basic
- Use a Next Generation / UTM Firewall with web filtering and antivirus. We recommend Fortinet FortiGate firewalls in all cases.
- Use a secure DNS / internet gateway product such as Cisco Umbrella. We provide Umbrella to all our IT support and managed security clients.
- Enable Logging and Alerts. You need to know about the activity and anomalous behaviours taking place!
- Strictly control outbound access and enable SSL inspection.
- Rules
- Develop the firewall policy with least privilege in mind (i.e. start with no internet access and work back to the point where people can work).
- Do not use rules such as ‘Allow All’ or ‘Allow Anywhere’.
Advanced
- For Remote-Access, consider the use of ZTNA over traditional SSL or IPSec VPN
- Use time-based rules. Only allow internet access from your end-users in core business hours (but you need to ensure there is a way for systems to update).
- Where inbound access is required, consider the use of SSL VPN technologies and 2FA.
- Utilise SD-WAN to enhance security further.
- For inbound services, rather than allow from ‘Any’, instead use geographic restrictions. If your staff only access the VPN from the UK – limit access to the UK.
- Use services such as Data Leakage Prevention and IPS, to prevent data disclosure and zero-day attacks. See our article on DLP here.
- Consider a managed security service.
Printers
Printers are often overlooked when businesses are assessing their security.
Basic
- Change default credentials.
- Ensure firmware and software is up-to-date.
- Disable unnecessary services or features.
Advanced
- Enable PIN printing and print auditing.
Microsoft 365
Many small businesses now use Office 365 for e-mail, Sharepoint and Onedrive, therefore it is important to put in place some basic security controls
Basic
- Enforce MFA for all users who use Exchange Online.
- Disable legacy protocols (i.e. POP3, IMAP, etc.)
- Enforce strong passwords.
- Limit users who have Global Administrator access.
- Implement Microsoft’s recommendations to improve the Secure Score in the Microsoft Portal.
Advanced
- Use and enforce Conditional Access Policies.
- Deploy Intune on devices to ensure device compliance.
- Subscribe to Office 365 Defender and implement hardened security policies (i.e. safe attachments, safe links).
- Use Cloud-to-Cloud backups
Summary – Small Business IT Security
These are simple recommendations for you to consider in the contact of your small business (or enterprise) IT and network security.
If you would like to review the IT security, firewall or network security of your small business – contact our solutions team.
Manx Technology Group works with companies throughout the UK and Ireland to help implement, enhance, support and manage their IT environments. E-mail us today – sales@mtg.im, call +44 1624 777837 or complete the contact form on the right.




