We look at what defines an Internal Network Firewall (INFW) and how they compare to Next Generation Firewalls (NGFW).
Traditional firewalls that had UTM-type functionality (e.g. Web filtering, Intrusion Prevention, Antivirus) that often suffered from a poor performance such as low throughput, latency and inconsistent accuracy. As firewall technology evolved, as did their performance and scanning capabilities. The Next Generation Firewall (NGFW) term was coined to define a firewall that met the following criteria:
- Application and Layer-7 awareness (e.g. DPI – Deep Packet Inspection). The ability to identify applications and protocols by payload and not just the IP header. L7 recognition often includes SSL inspection.
- Intrusion Prevention System (IPS) capabilities. Where the firewall can identify malicious traffic, data breach attempts, unusual patterns and DOS attacks, the IPS can often include DLP (Data Leakage Prevention).
- High Performance. An NGFW must carry out its functions at near wire-speed, enabling multi-gigabit performance without slow-down.
- External Threat Intelligence. To receive updated threat intelligence, IP reputation insight and attack signatures, the NGFW must communicate with a threat intelligence network (e.g. FortiLabs).
These characteristics adequately define what qualifies an NGFW. The exact definition can vary depending on the analyst, vendor or industry commentator; but those four items are consistent across most definitions.
An NGFW system is often deployed within carrier or service provider networks, the datacentre environment, virtual and cloud environments or at the enterprise network edge.
Internal Network Firewall (INFW)
The Internal Network Firewall (INFW) is not necessarily a new technology, but a specific application of the Next Generation Firewall (NGFW) platform.
In most IT or hosted environments, we can classify traffic patterns as:
- North to South – Traffic going from the LAN to the Internet, and vice-versa.
- East to West – Traffic internal to the organisation, routing server-to-server, server-to-client or client-to-client but not leaving the organisation. East to west traffic can be between IP subnets or routed VLAN interfaces (typical in many enterprises with L3 switches).
The exact ratio of the north to south and east to west will vary from business to business, and it will depend on the relevant IT environment. Figures from Gartner suggest 77% of traffic is East to West, while 17% is North to South (The remaining 6% is between sites).
These statistics set out the reason for an Internal Network Firewall (INFW); most traffic in an organisation or virtualised environment is East to West, that comes as no surprise. One of the key topics I have discussed in previous articles and is a recurring theme with our clients is the safeguarding against data leaks, data theft, data breaches, malware and APT (advanced persistent threats) – all of which can fall under the umbrella of cyber-security.
The most common location for a firewall is at the network-edge, NGFW devices deployed in this manner can identify north-to-south threats, viruses and data breaches. The type of risk could include “Botted hosts” trying to phone home (identified through DNS traffic, IPS signatures or IP reputation patterns). It could be a user accessing a website trying to exploit a bug in Adobe Acrobat, the possibilities are endless, and ever-growing by the day. Modern threats are intelligent; they can use methods such as stenography, encryption and obfuscation to hide their presence. An innocent looking JPEG image that has been posted to a website could contain corporate data. The threat landscape has changed.
Fortinet, a leader in the firewall marketspace, recognise the importance of an INFW in a modern business network.
What about the internal traffic?
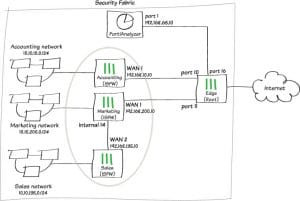
Perimeter devices may identify external threats, what about those moving or probing within your internal network? Threats could be shifting between sites or subnets, in your virtualised networks and server-farms, on your virtualised LAN segment! The infection vector could have been USB, a mobile device, a laptop or an exploit bundled in with custom software.
The enumeration of your systems, data assets and network topology will all take place within your internal network environment.
This surveillance process could be automated and undertaken by the malware, or equally – it could be performed by a rogue employee or an individual with (unauthorised) access to your network or systems.
If this traffic does not traverse your edge security device – how can you detect them?
The internal border-crossing of your network
The ideal place for an INFW is literally in the middle of your network or networks. There are many deployment methods; the most suitable method will depend on your network topology and your network throughput. MTG design and deploy service provider and enterprise networks, so we are often involved in the design and configuration of systems.
- Transparent Bridge / Inline. This mode offers the best balance of security and simplicity from a network reconfiguration standpoint. In this scenario, the firewall is connected between network segments transparently. The bridge could be using 1GE, 10GE and 40GE interfaces, with the respective fibre/copper derivatives where appropriate. Network security policies can be enforced, even in L2 operation. With the inline operation, the device can intervene, block and alert you to risky traffic patterns or data leak attempts.
- Sniffer Mode. Your network switches can be configured to mirror VLANs or interfaces and send this mirrored traffic to the firewall similar in operation to an IPS probe. The disadvantage of this mode is it cannot intervene with the traffic flow, observe and alert.
- Active Deployment. This mode has the highest levels of security, visibility and enforcement – but requires a level of network reconfiguration. The firewall can replace your SVI/VLAN interfaces on your switching fabric, it can partake in your L3 routing protocols (e.g. BGP/OSPF) or provide physical interfaces and routing between subnets. Network security policies can be applied to interfaces (VLAN or physical), and all traffic can be scanned.
Once you have deployed an INFW, your business can be safe in the knowledge its internal (east to west) traffic is scanned for threats, viruses, intrusion attempts and data leakage activity.
An enterprise can opt for centralised deployment mode, clustered deployments or distributed environments (a device per site).
The INFW can also integrate with our range of endpoint protection and Sandboxing solutions, for advanced payload analysis.
What about small business?
INFW solutions are not just for the enterprise and are ideally suited for a small business network environment. The throughput capabilities of modern firewalls (i.e. >1GE) make them suitable for policing traffic between internal network segments. Useful for PCI compliance.
Speak to MTG about INFW
If your business requires an INFW speak to MTG. Our team of network and security engineers can design and implement an INFW solution for your network environment. Key capabilities include:
- Network integration options.
- 1GE, 10GE and 40GE network support.
- Copper, optical and VLAN interfaces.
- High throughput (from 100Mbps to 40Gbps+).
- Transparent, sniffer and active deployment mode.
- IPS (Intrusion Prevention)
- Antivirus and Sandboxing
- DLP (Data Leakage Prevention)
- Traffic shaping and QOS
- Application control and reporting
- IP Reputation and threat intelligence
You can call +44 1624 777837, e-mail sales@mtg.im or use the contact forms on our website.
Further Reading
- Managed Firewalls and Network Security (Service)
- How to deploy an Internal Network Segmentation Firewall
- Small Business Firewall Guide
- Best Small Business Firewall/Router




