Most businesses reach a point where their firewall needs attention. It may be ageing, poorly performing, no longer fit for purpose, or simply not aligned with how the business now operates across cloud services, remote users, and multiple sites.
At that point, organisations have a choice. You can replace the firewall as a traditional project, or you can move to a fully managed firewall delivered as a service. Both improve security. One significantly reduces cost, risk, and ongoing effort.
Our approach starts with understanding the business, then designing the firewall solution around risk, users, and operations – not around hardware. For many organisations, Firewall-as-a-Service becomes the natural choice once the true cost of ownership is understood.
Start With the Business, Not the Firewall
Before touching policy or hardware, we focus on how the organisation actually operates:
What systems and cloud platforms are in use?
Existing firewall rules are often used as a reference point, but rarely as a blueprint. In many environments, policies have grown organically over years and no longer reflect the real business or threat landscape. Our goal is to align network security with business risk, usability, and operational reality – not simply replicate legacy configurations.
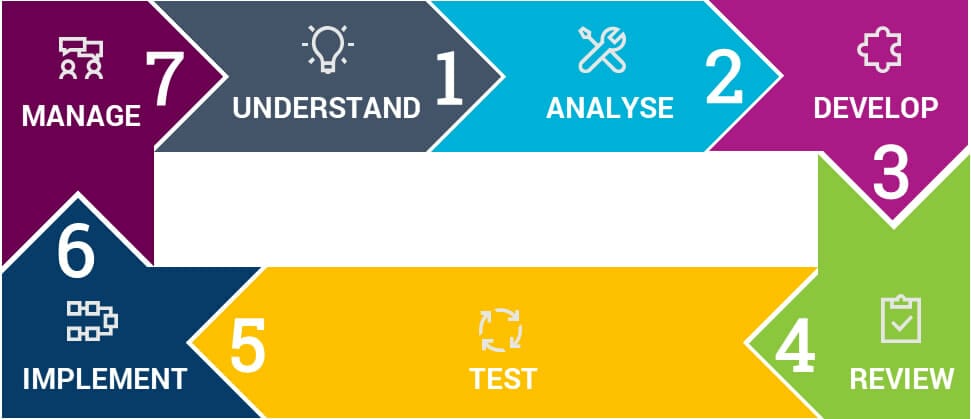
1 – Understand
We develop a working understanding of your organisation, systems, users, and data flows. This includes identifying business risk, regulatory drivers (e.g. CE/CE+, PCI), and reputational exposure.
Firewalls exist to mitigate business risk, not because they are “best practice”. A clear business case underpins every design decision.
2 – Assess and Analyse
We assess your existing firewall policy and how it maps to the requirements identified in step one. Key questions include:
This phase highlights gaps and informs the new design.
3 – Design and Develop
We design a security policy optimised for Sophos XGS firewalls, covering:
Where Sophos endpoints are in use, we also design around Security Heartbeat. This allows the firewall and endpoints to share real-time health status, enabling the firewall to:
Attention to these details, combined with platform-specific experience, is what prevents painful cutovers, unstable policies, and post-migration surprises.
4 – Review
We conduct a joint review of the proposed design, allowing for final validation and further policy cleanup before deployment. This step often removes years of technical debt.
5 – Test
Before going live, we test the configuration against agreed scenarios:
Testing continues throughout implementation and into live service as business needs evolve.
6 – Implement
Cutover is performed during an agreed maintenance window, typically outside business hours. We validate traffic flows, performance, and security controls, making adjustments as required. Once live and accepted, MTG remains on hand to resolve any migration-related issues.
Testing continues throughout implementation and into live service as business needs evolve.
7 – Manage (FWaaS)
Once deployed, the firewall is fully managed as part of our IT-as-a-Service (ITaaS) model. This includes:
Sophos XGS as Firewall-as-a-Service (FWaaS)
We deploy Sophos XGS firewalls as a monthly service, removing the need for large upfront capital spend.
This makes firewall replacement straightforward, affordable, and operationally simple.
Demonstrating Value and ROI
Modern firewalls should not be “expensive boxes at the edge”. They should provide continuous insight into how the network is being used, what applications are in play, and where real risk exists. Visibility is what turns a firewall from a sunk cost into an operational security control.
Sophos XGS delivers deep visibility into traffic, applications, and threats, alongside clear reporting for management and compliance. Combined with protection against modern attacks such as ransomware, malware, and lateral movement, this allows security effectiveness – and ROI – to be demonstrated clearly and credibly to stakeholders.
Engage the experts
We design, supply, migrate, and manage firewalls for small businesses through to complex multi-site environments. Engagements range from consultancy and migration projects to fully managed firewall services delivered under ITaaS.
Manx Technology Group deliver managed firewall services across the UK, Europe, the US, and Asia.
If you are considering a firewall refresh or want to move to FWaaS with Sophos XGS, get in touch to discuss what that looks like for your environment.