Do you have Conditional Access? If you’re not sure, or you’re relying solely on Multi-Factor Authentication (MFA), you could be leaving your business vulnerable to cyber threats. Conditional Access (CA) is a game-changing security measure, especially for businesses using Microsoft 365 (M365). But what exactly is it, and why should it matter to you?
Why Conditional Access is More Than MFA
Many businesses rely on MFA to verify users’ identities. But MFA alone isn’t always enough. Cybercriminals are getting smarter, and phishing attacks are becoming more sophisticated. This is where Conditional Access takes things to the next level by adding contextual controls.
For example, imagine you’ve implemented MFA in your business and secured your M365 environment. It ensures that users verify their identity with a second factor—great. But what happens if an attacker has stolen an employee’s credentials and manages to bypass MFA? Conditional Access steps in to block access based on other conditions like location, device health, or security posture.
Here are some examples of how Conditional Access improves security:
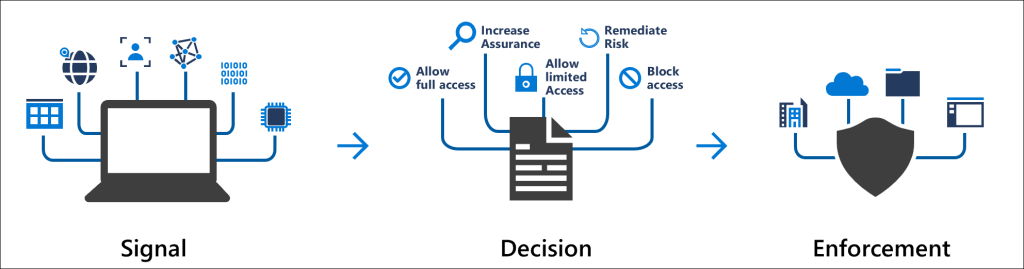
I have MFA – do I need Conditional Access?
While Multi-Factor Authentication (MFA) is a great first step in securing your business, it’s no longer enough on its own. MFA ensures that users verify their identity, but it doesn’t account for the context of access attempts, such as the device being used, its security status, or where the request is coming from. Conditional Access (CA) adds these crucial layers of protection by allowing you to set rules based on conditions like location, device compliance, and user behaviour. With CA, you can prevent risky logins even if someone passes MFA, making your security framework far more robust and adaptive to modern threats.
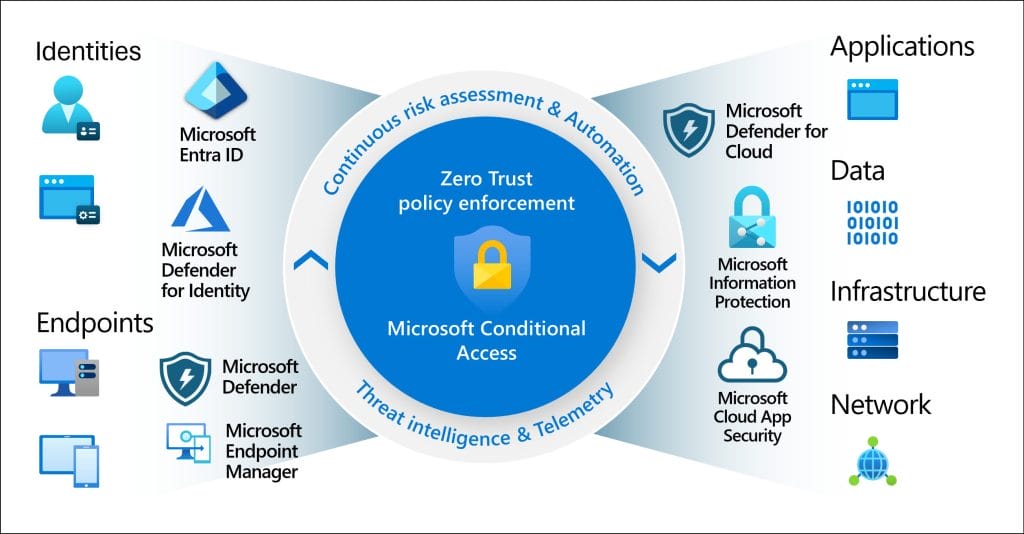
How Do I Know if I Have Conditional Access?
If you’re a business owner, the easiest way to find out if your organisation is using Conditional Access (CA) is to ask your IT department or Managed Service Provider. They can confirm whether CA policies are in place. However, there are some signs that might indicate you already have Conditional Access. Y
ou or your staff might be prompted for additional security measures, such as requiring Multi-Factor Authentication (MFA) only when logging in from certain devices or locations. You might also find that access is restricted from untrusted devices or while travelling, requiring extra verification or blocking access altogether. If you receive security notifications about risky sign-ins or access being blocked due to security concerns, these are strong indicators that Conditional Access is active and protecting your business environment.
Why Does Conditional Access Matter?
As cyber threats evolve, businesses must adapt to stay ahead. Conditional Access ensures that your systems are proactively protected, allowing only safe, trusted access. By implementing CA, you gain control over who can access your systems, from where, and under what conditions.
For businesses with employees working remotely, or with sensitive data stored in the cloud, Conditional Access is vital. It gives you the peace of mind that your data is protected not only by MFA but also by a system that checks and verifies every login attempt based on multiple layers of security.
Examples
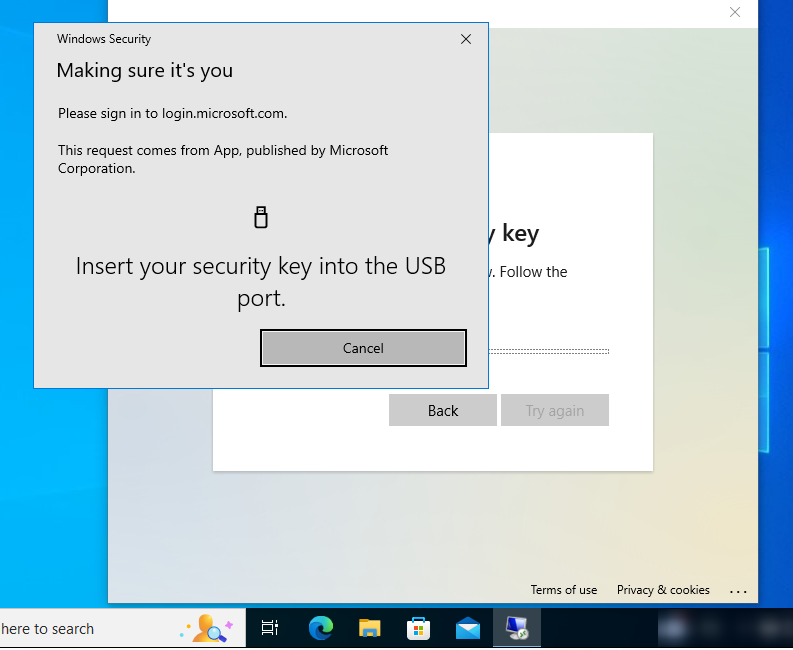
FIDO2: Even better Security..
To further enhance your security posture, FIDO2 authentication can streamline access for users while eliminating the risks associated with traditional credentials. Unlike passwords, which can be phished or stolen, FIDO2 keys are hardware-based and require physical presence to unlock access.
This makes it an ideal solution for protecting high-value accounts, remote-workers, and sensitive data. Moreover, FIDO2 integrates seamlessly with Conditional Access, allowing you to enforce strict security policies without compromising user experience. By adopting this combination, you’re not just adding layers of security—you’re actively future-proofing your business against evolving cyber threats.
FIDO2 tokens are inexpensive, and work with desktops and laptops, and also Android and iPhones (USB or NFC).

Steps You Can Take Today
Here are a few steps to strengthen your business’s security using Conditional Access:
If you’re unsure how to get started, we can help. We specialise in setting up Conditional Access and other security measures for businesses using M365, including Managed IT Security, Network Security, and Security Awareness Training.
Check your subscription
NOTE: Conditional Access requires M365 Business Premium, or Entra-ID P1 or above. This is why we encourage all of our customers to upgrade for enhanced security.




