Once malware or a malicious exploit bypasses your defences, it may establish a “persistent foothold,” a hidden mechanism that allows it to survive reboots or log-offs. Persistent footholds are particularly dangerous because they allow hackers continued access to your systems, sometimes unnoticed for months or even years. Detecting and removing these footholds requires advanced solutions like Managed Detection and Response (MDR) or Extended Detection and Response (XDR) software.
How does a persistent foothold work?

A foothold is typically created when an attacker gains initial access to your system, often through phishing emails, drive-by downloads, or exploited vulnerabilities. Once inside, the malware establishes persistence by using tactics such as scheduling tasks, adding malicious registry keys, or installing drivers that automatically execute when the system reboots. (You can read more about this on Crowdstrike).
This mechanism allows the attacker to retain control and access over time, making your business vulnerable to further attacks, data theft, or even ransomware deployment. With MDR or XDR, such as Sophos MDR or Huntress, these footholds are quickly identified and neutralized before they can cause more damage.
Examples of Persistent Footholds
In a Windows environment, common persistence mechanisms include:
- Scheduled tasks that automatically run scripts
- Registry keys that load malware during startup
- Startup items that reinstall malware after reboot
- Malicious system drivers
Once established, the malware can function as a sleeper agent, ready to reactivate on command or sell access to other cybercriminals.
Why Traditional Antivirus May Not Be Enough
While antivirus software can stop many forms of malware, it often falls short when dealing with sophisticated footholds. Why? Because the persistence mechanism itself may not be flagged as malicious. It could be a seemingly benign script or system task that only becomes dangerous when activated by the attacker.
Modern threats demand modern defences—this is where MDR and XDR step in. These systems monitor your environment 24/7 and use AI-driven analytics to detect and respond to even the subtlest signs of a foothold or intrusion.
What MDR/XDR Can Do for You
- Proactive Threat Detection: MDR/XDR platforms continuously scan for threats like persistent footholds.
- Rapid Response: When a threat is identified, SOC (Security Operations Centre) teams can respond immediately, often containing the issue before it escalates.
- Comprehensive Coverage: From ransomware to data breaches, these systems cover your endpoints, servers, cloud workloads, and more.
- Cost Efficiency: By preventing expensive downtime or ransom payments, MDR/XDR offers an excellent return on investment.
At Manx Technology Group, we offer sophisticated MDR solutions designed to protect your business against persistent threats. Whether you’re looking to bolster your cybersecurity or require a full IT infrastructure review, we can help.
The Importance of Timely Detection
According to Sophos, the average dwell time (the time an attacker remains undetected) is around 11 days, which gives cybercriminals ample time to steal data, install ransomware, or sell access to your systems. Don’t let a persistent foothold be your weak point. Act now.
How We Can Help
We provide advanced MDR services that include:
- 24/7/365 monitoring and response through a dedicated SOC team
- Automated threat remediation
- Custom threat intelligence designed for small to medium businesses
- Regular security audits and compliance checks
With our MDR or XDR solutions, you can ensure that persistent footholds are not lurking in your environment. These tools integrate seamlessly with your existing infrastructure, providing robust protection without disrupting your operations.
Recommendations for Small Businesses
- Implement MDR/XDR for continuous monitoring and response.
- Ensure regular patching and updates to close vulnerabilities.
- Educate employees about phishing and social engineering attacks.
- Use multi-factor authentication (MFA) for all critical systems.
- Regularly review and harden your system configurations.
Where does MDR software fit into my existing security architecture?
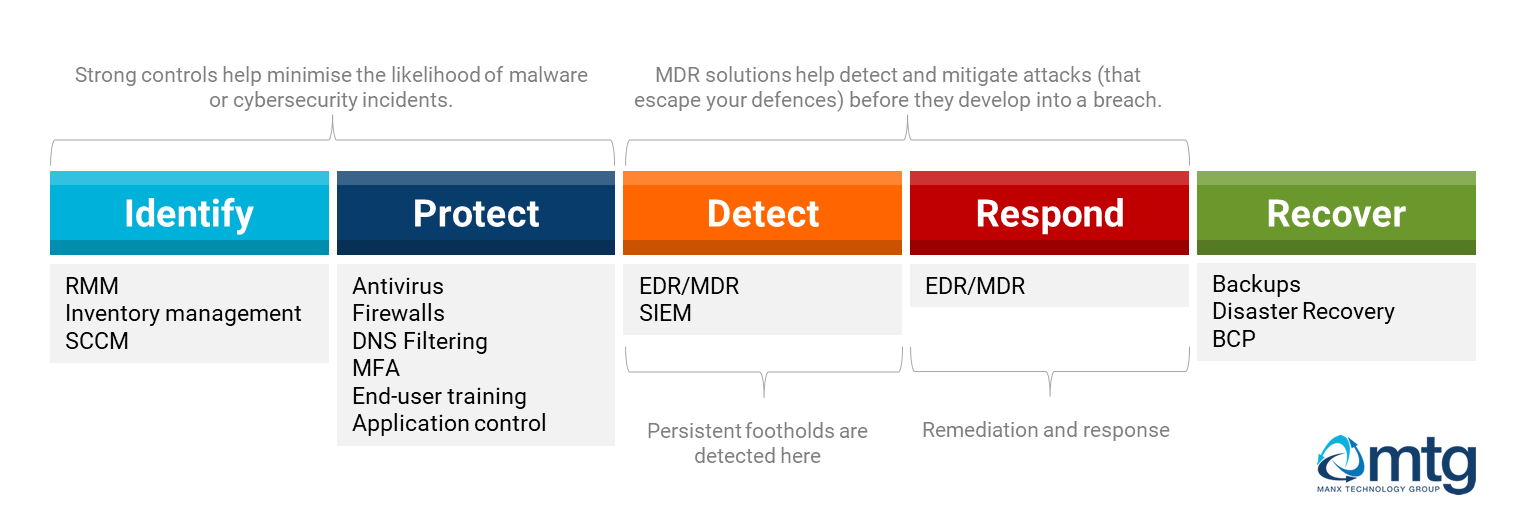
The NIST Cybersecurity framework defines five core functions, also known as the Framework core.
- Identify
- Protect
- Detect
- Respond
- Recover
EDR/MDR solutions provide stronger coverage in the detection and response areas – helping to identify threats proactively and helping you avoid a worst-case scenario.
What else do I need to consider?
As with everything when it comes to cybersecurity, you need to focus on all aspects of information security:
- Patching and systems updates.
- End-user training.
- Configuration hardening.
- Authentication and 2FA.
- etc.
It is also worth noting that more and more cyber insurance policies recommend, or mandate, the user of EDR/MDR software.
Ready to Secure Your Business Against Persistent Footholds?
Contact us today to implement MDR/XDR and protect your systems from hidden threats.