While traditional antivirus solutions have long been a cornerstone of protection for businesses of all sizes, the rapidly evolving threat landscape requires more advanced and comprehensive security measures. Enter modern endpoint protection solutions, such as EDR, XDR, an MDR, designed to address the complex challenges that today’s small businesses face.
Introduction
This article explains the differences between the solutions and why businesses of every size should use one of the most advanced endpoint solutions.
But what exactly are these modern equivalents, and how do they differ from the traditional antivirus software you’ve come to rely on? This article will explore the key differences between traditional antivirus solutions and their modern counterparts – helping you understand their unique capabilities and benefits. Armed with this knowledge, you’ll be better equipped to make informed decisions about the best cybersecurity strategy for your small business, ensuring that you stay one step ahead of cybercriminals and protect your valuable assets.
Antivirus or Endpoint Security
Antivirus software initially worked on the principle of virus definitions and rudimentary heuristics to detect computer viruses and malware (i.e. trojans). Antivirus software was good at identifying known malware through known signatures, but its utility has dwindled in recent years as threats become more sophisticated.
Modern endpoint protection solutions, such as EDR, XDR, and MDR, go beyond traditional AV by using advanced techniques like behavioural analysis, machine learning, and artificial intelligence to detect and respond to a broader range of threats, including zero-day attacks and advanced persistent threats (APTs).
EDR (Endpoint Detection and Response):
EDR is a security solution that monitors and detects potential threats, anomalous activities, and security incidents at the endpoint level. It collects and analyses data from endpoints to identify potential threats and provides IT teams with the necessary information to respond to and remediate incidents. EDR solutions typically offer real-time monitoring, threat hunting, and incident investigation capabilities.
XDR (Extended Detection and Response)
XDR is an evolution of EDR, as it extends the detection and response capabilities beyond endpoints to include other security layers such as network, cloud, and email. XDR is designed to provide a more comprehensive and integrated security solution by correlating and analysing data from multiple sources. This broader visibility helps security teams to detect and respond to advanced threats more effectively, reducing the time it takes to discover and remediate incidents.
XDR platforms may bring in events from Microsoft 365, Firewalls and other third-party identity providers (i.e. Okta).
MDR (Managed Detection and Response)
MDR is a service provided by third-party cybersecurity vendors offering EDR or XDR capabilities in combination with their security expertise.
Vendors typically handle the deployment, management, monitoring, and incident response on behalf of the organization. They actively analyse the collected data, detect threats, and notify the organization of potential security incidents, often providing recommendations or directly remediating the issue.
MDR services help organizations with limited security resources or expertise to maintain a strong security posture. By outsourcing these tasks to an MDR provider, organizations can focus on their core business functions while benefiting from the expertise of a dedicated security team.
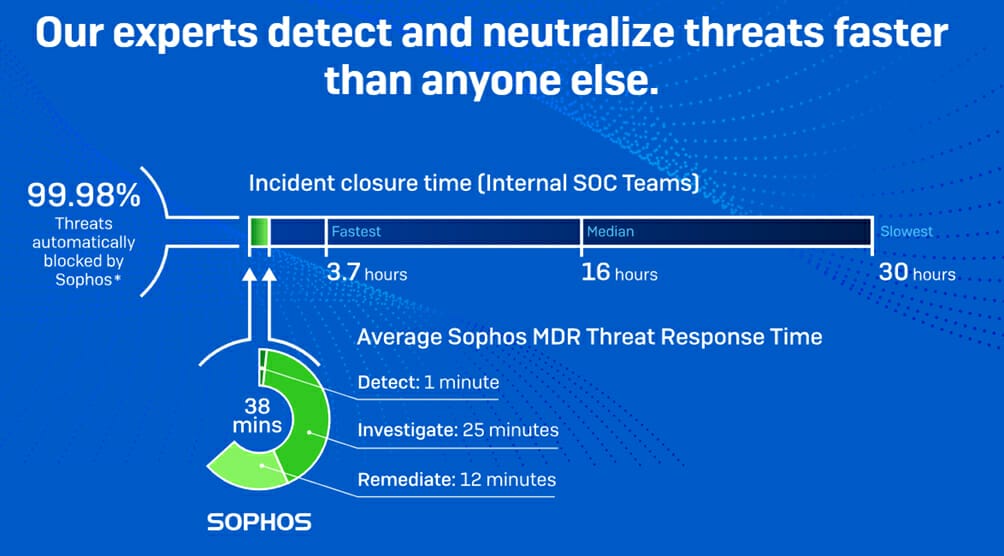
MTR (Managed Threat Response)
MTR is another form of managed security service that is similar to MDR. The primary difference between MTR and MDR is that MDR providers take a more proactive approach to threat hunting and response. MTR services involve continuous monitoring, advanced analytics, threat intelligence, and proactive threat hunting to identify and mitigate threats before they can cause significant damage.
Features
Detection
Using the information gathered through the EDR software, AI and detection engines can correlate events to spot unusual activity that may indicate a threat or exploit. EDR technology correlates events and analyses sequences of events to see if they match a known IOA (an indicator of attack) before generating alerts or triggering an intervention. EDR detection is automatic, but engineers can also conduct their threat hunts to identify threats.
Containment
Upon detecting a threat, modern EDR platforms will terminate the offending process, isolate the system and take additional steps to safeguard the system.
Investigate
The data gathered by EDR is analysed in real time and can be used to investigate historical activity and changes in your systems. Examples would include:
- Files created or modified.
- Process executions.
- New user accounts, user account modifications or password changes.
- Changes to user groups or permissions.
- The use of administrative tools.
EDR data allows the operator to understand how, when and why something occurred in the IT environment.
Remediation
If the EDR platform detects an incident, it can provide remediation advice explaining how to mitigate and remove the security threat.
EDR solutions
EDR solutions include Sophos Intercept-X with EDR, Microsoft Defender for Endpoint, Sentinel One, Crowdstrike Falcon and VMWare CarbonBlack EDR. You can find more EDR vendors over at Gartner.
What services would you recommend?
As expertise and focus are required to get the most value from an EDR/XDR platform, we recommend our customers invest in an MDR solution.
MDR is a much more cost-effective solution than a fully-fledged SOC, and for the price, it provides much higher levels of protection for your IT systems. With the growing ransomware threat, insider threats and more sophisticated attacks – MDR provide far greater detection capabilities and expert response.
Sophos Intercept-X Advanced with MTR
 Sophos Intercept-X Advanced with MTR is installed on your desktops and server systems. Following an initial onboarding process (where system configuration and security posture is analysed), your organisation is protected by the Sophos MTR team.
Sophos Intercept-X Advanced with MTR is installed on your desktops and server systems. Following an initial onboarding process (where system configuration and security posture is analysed), your organisation is protected by the Sophos MTR team.
From then on, all events, processes, network connections and user activity are logged by the Sophos EDR platform and subject to various AI and machine learning algorithms to detect threats. If a threat or IOC is detected, the Sophos MTR team will automatically intervene and look to remediate the threat.
Sophos Intercept-X Advanced with MTR is a monthly subscription, with per-device subscriptions for desktops/laptops and servers.
Huntress
 Huntress Labs offers an MDR platform backed by a team of 24/7 threat hunters. Huntress focuses on persistent footholds, which include exploits, malicious software, or configuration changes that would otherwise allow an attacker to access and remain on your systems.
Huntress Labs offers an MDR platform backed by a team of 24/7 threat hunters. Huntress focuses on persistent footholds, which include exploits, malicious software, or configuration changes that would otherwise allow an attacker to access and remain on your systems.
Huntress can be used alongside existing antivirus solutions to provide enhanced MDR functionality. If the Huntress SOC detects a foothold or similar anomaly, their team of threat hunters will automatically respond, either neutralising the threat or providing you with remediation advice.
Find out more
Don’t wait until it’s too late to safeguard your small business from growing cyber threats.
As the digital landscape evolves, so must your cybersecurity strategy. By embracing modern endpoint protection solutions like EDR, XDR, MDR, or MTR, you can proactively defend your organization against advanced attacks and minimize potential damage. Invest in your business’s future by evaluating your security measures and exploring the benefits of these cutting-edge solutions.
Please speak to our team today to discuss your needs and determine the best approach to secure your business in this ever-changing digital world. Remember, staying vigilant and adapting to new security technologies is crucial for your small business’s continued success and growth.